Types of Endpoint Security Services
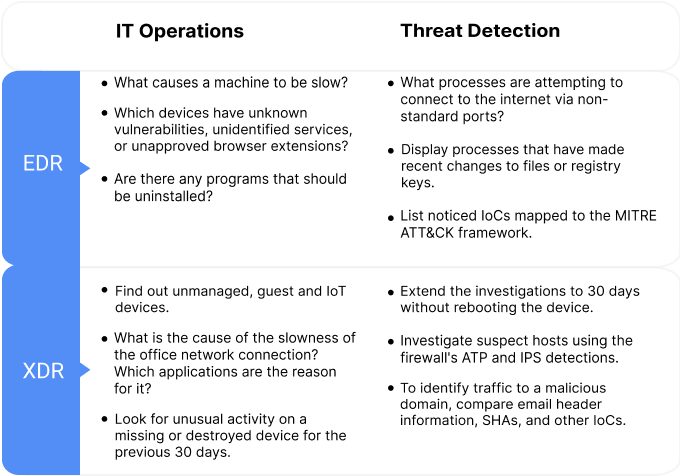
Endpoint Detection and Response (EDR)
Endpoint detection and response (EDR) tools are designed to increase and improve detection, investigation, and response capabilities for endpoint security.
EDR provides information about what has occurred in the past and what is currently occurring on the endpoints. Threats can be tracked to detect active attackers and IT operations can be leveraged to maintain strong and effective IT security hygiene. When a problem is discovered remotely, i̇t enables a corresponding rapi̇d response to limit the damage.
EDR prevents breaches from occurring by starting with the strongest protection possible. When hunting down threats and strengthening your IT security operations posture, EDR gives you valuable tools to ask detailed questions and improve your security standing.
Extended Detection and Response (XDR)
XDR integrates firewall, email, network, email, cloud, mobile and other data sources in addition to endpoints and servers. It provides a comprehensive picture of your company’s cybersecurity posture, with the option to drill down into granular detail if necessary.
Using XDR, you can swiftly identify, isolate, and eliminate a threat by comparing attack indicators from numerous data sources. XDR allows you to locate unmanaged, guest, and IoT devices throughout your organization’s network. It also enables you to identify any office network problems, as well as the applications that are causing them.
Managed Threat Response
Managed Threat Response (MTR) facilitates threat hunting through the use of proactive 24/7 tracking by our threat analysts, making the potential impact and context of threats to your business visible to you at any time.
MTR Initiates actions to remotely disrupt, contain, and neutralize threats on your behalf to stop even the most sophisticated threats. It empowers continuous Improvement by addressing the root cause of recurring incidents to stop them from occurring again, rather than simply one-time fixes.